CyberDefenders - Series (Malware Traffic Analysis 2 - Packet Analysis)
Introduction
The Digital Forensics & Incident Response (DFIR) field is one, where you must keep learning to stay current with the latest development and to keep your skills sharp. Therefore I've decided to start working on some challenges that are delivered through CyberDefenders. It's a great place to work on challenges and to keep developping yourself.
The Challenge
This blog describes the 'Malware Traffic Analysis 2' challenge, which can be found here.
Tools used for this challenge:
- Brim
Write-up
My write-ups follow a standard pattern, which is 'Question' and 'Methodology'. I choose this format, because it allows you to be able to follow along and try this challenge for yourself. I have choosen not to disclose the answer here, since it's also a competition and I don't want to spoil the integrity and fun of competing.
Question 1
What is the IP address of the Windows VM that gets infected?
Methodology
Same as last time, the question starts with a relative easy question for the analyst to figure out what machine got infected. The question itself has a big hint saying we're looking for a Windows VM. I opened the capture in my new favorite tool for network analysis NetworkMiner and immediately in the Hosts overview you will find only one Windows VM.
Question 2
What is the MAC address of the infected VM?
Methodology
One of the great features of NetworkMiner is that you'll see all host details in one overview, so if you located the only Windows VM, you can also see the MAC address.
Question 3
What are the IP address and port number that delivered the exploit kit and malware?
Methodology
To answer this question I made use of a new tool in my arsenal called Brim, see section above for a download link. Brim is able to parse pcap files and create Zeek logs (formerly Bro) from it. It also supports Suricata rules to automatically detect potential bad activity. I've installed Brim and used the Youtube video created by CyberDefenders to configure it correctly. After installation you can import a pcap file and it will automatically provide you with a search interface to investigate the Zeek logs. For this pcap file there were also some alerts generated. Using the following query, you will get an overview of the alerts.
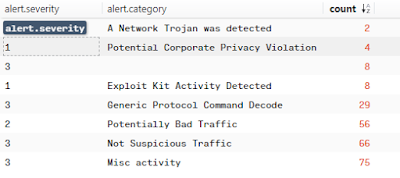
event_type=alert | count() by alert.severity,alert.category | sort count
It should look something like this:
Hopefully you'll notice the alert 'Exploit Kit Activity Detected', if you want to search for that alert you can use the following query:
event_type=alert alert.category="Exploit Kit Activity Detected"
You can inspect the individual alerts by right-clicking on them and selecting 'Open details' analysis of the individual alerts should provide you with the right answer.
Question 4
What are the two FQDN's that delivered the exploit kit? comma-separated in alphabetical order.
Methodology
Now that we know what IP address was used we need to find out the Fully Qualified Domain Name (FQDN) that delivered the exploit kit. There are several methods to answer this question, the easiest one is going to NetworkMiner and in the host details for the IP address that delivered the EK it automatically shows you the FQDN's. Another method is using Brim you can search for the IP address and you'll find several HTTP GET requests that contain the FQDN. An easy query to answer this question is shown below, I've removed the IP address, but if you made it to this point you should have it:
ip-address method="GET"
Question 5
What is the IP address of the compromised web site?
Methodology
To answer this I went back to the IP address of the machine that was compromised and did a search on the IP. I also used a little bit of my knowledge on these types of attacks and in most incidents like this a user visits a websites and (accidently) downloads an exploit kit. I used the following search in Brim to see all HTTP related traffic from the infected machine:
172.16.165.132 _path="http"
Next was looking at the earliest events to see what domain/website was visited and based on that you should find one IP address that keeps coming back and is actually used to retrieve lots of 'interesting' files.
Question 6
What is the FQDN of the compromised website?
Methodology
Using the answer from the previous question you should also be able to see the FQDN in the HTTP traffic to answer this question.
Question 7
What is the name exploit kit (EK) that delivered the malware? (two words)
Methodology
Earlier in this challenge in Question 3 we figured out what the IP address was of the machine that was delering the EK. Now you can really leverage the power of Brim, by filtering on the IP address and next start filtering on alerts generated by this IP address and the answer will be revealed to you :)
Question 8
What is the redirect URL that points to the exploit kit landing page?
Methodology
This one took me quite some time, I used several methods without results for instance seaching on the IP address of the compromised website to see if I could find something there. Another method was to analyse a lot of the HTTP traffic manually in hindsight this how I could've found it, but in the end I was thinking a bit too difficult. The key to the answer was analyzing the alerts generated by Brim. I found that there were several servers hosting the EK and one of them showed several alerts and HTTP traffic towards an interesting URL from the domain that we identified in Question 6.
Question 9
What is the IP address of the redirect URL that points to the exploit kit landing page?
Methodology
The answer to question 8 shows the domain and the IP address so this should be an easy one.
Question 10
Extract the malware payload (PE file) from the PCAP. What is the MD5 hash?
Methodology
For me the easiest method to export files is still good old Wireshark. If you go to File-Export Objects-HTTP you can easily filter on application files, since the question is asking for a PE file. There is only one PE file in the dump. After you download it calculate the hash and you got yourself another answer. I always use Powershell to calculate hashes for individual files using the following command:
$PS>Get-FileHash -Algorithm MD5 <path-to-file>
Question 11
What is the CVE of the exploited vulnerability?
Methodology
This is the great thing about having Brim running and having added Suricate rules in Brim. It automatically detects suspicious/malicious activities. If you filter on alerts you should be able to figure this one out.
Question 12
What is the mime-type of the file that took the longest time (duration) to be analyzed using Zeek?
Methodology
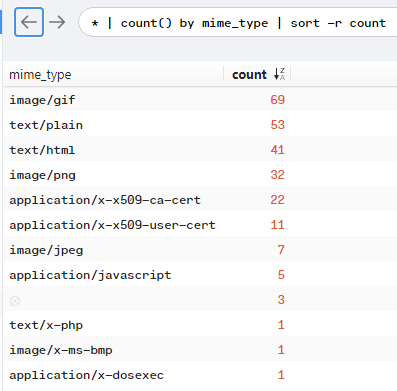
This is more a question for people that are already familiair with Brim/Zeek as the question is more metadata related. I'm learning Brim/Zeek on the fly with this challenge, so this took me longer than it probably should as the answer is pretty easy. What I did was looking around in the data itself to see if I could find fields that relate to process time or something similiair. This exercise wasn't that succesfull in the beginnen so then I started looking for ways to get information about the mime-type of a file. If you execute the following search you'll get information on the various mime-types present in the dataset:
* | count() by mime_type
If you look at the answer format on the website of CyberDefenders you'll already see the answer using the above query. I wanted to dig a little deeper so I opened one of the mime-types present and upon further inspection of the various metadata fields I found a field showing you how long it took Zeek to process the file. Finally combine the mime-type query with the other field showing you the processed time you'll find the answer.
Question 13
What was the referrer for the visited URI that returned the file "f.txt"?
Methodology
Fun question, what I did was search for the filename in Brim and the beauty of Brim is that if you go over the entries it will highlight the fields that it parsed. This allows you to find the referrer for that file in a blink!
Question 14
When was this PCAP captured?
Methodology
This one is pretty easy just look at the properties of the file in Wireshark-Statistics or if you look at the events and what timeperiod they cover you can also answer this.
Question 15
When was the PE file compiled?
Methodology
If you remember we've had to answer a question about the payload in Question 10. So we can use that to further inspect the file to load it in something like Pestudio. However, it's far easier Zeek automatically extracts PE files and Brim makes it searchable. It even shows you stuff like compilation time, architecture, section names all the basic stuff you would like to know about an executable. So go ahead and start searching for the PE file and you'll find the answer in no-time.
Question 16
What is the name of the SSL certificate issuer that appeared only once? (one word)
Methodology
Again it almost feels like Brim is cheatmode try searching for mime-types related to a certificate. By know you should know that you can easily count on fields by right-clicking, this should help you find the SSL certificate that is only present once.
Question 17
What were the two protection methods enabled during the compilation of the present PE file? Format: comma-separated in alphabetical order
Methodology
To answer this one I went back to the search I used for Question 15 and I was able to answer this question using the data that was parsed by Zeek and shown by Brim.
Conclusion
Mission accomplished! All questions answered what a great challenge and what I really like about these challenges is to play around with different tooling and learn new things. For this one I tried to answer all questions with Brim, which is an awesome free tool please check it out. Also come back next week for a new write-up!